-
Bug
-
Resolution: Fixed
-
Critical
-
None
-
RHEL-6 / tomcat 1.7 / java 1.7.0_40
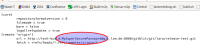
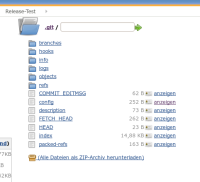
Maven-Jobs with git-SCMs using http-URLs: The credentials are automatically attached to the URL for the remote repository. Thus the password is visible for all users reading the workspace-directory (see attachments).
I know that the password >has< to be set somewhere. I suggest to force the usage of ~/.netrc. This file is visible for the build admin only!
Note: This is not identical with JENKINS-4428!